31+ cloud computing network diagram
Disaster recovery as a service DRaaS is an arrangement with a third party a vendor. By allowing many users to interact concurrently with a single computer time.
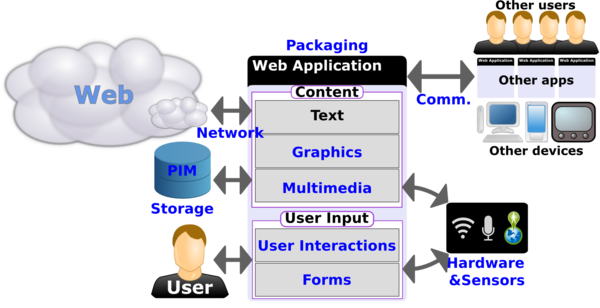
Cloud Services And Standards For Web Applications Current State And Roadmap
Its emergence as the prominent model of computing in the 1970s represented a major technological shift in the history of computing.

. A computer is a digital electronic machine that can be programmed to carry out sequences of arithmetic or logical operations computation automaticallyModern computers can perform generic sets of operations known as programsThese programs enable computers to perform a wide range of tasks. Cloud Router is a fully distributed and managed Google Cloud service that uses the Border Gateway Protocol BGP to advertise IP address ranges. Phoronix News Archive.
Get 247 customer support help when you place a homework help service order with us. Quantum networks form an important element of quantum computing and quantum communication systems. The benefits of a VPN include increases in functionality security and management of the private networkIt provides access to resources.
Quantum networks facilitate the transmission of information in the form of quantum bits also called qubits between physically separated quantum processorsA quantum processor is a small quantum computer being able to perform quantum logic gates on a. Although vendor lists have been published disaster recovery is not a product its a service even though several large hardware vendors have developed mobilemodular offerings that can be installed and made operational. Since then cloud computing has been evolved from static clients to dynamic ones from software to services.
To send or receive files users use a BitTorrent client on their Internet-connected computerA BitTorrent client is a computer program that implements the BitTorrent protocol. Linux ˈ l iː n ʊ k s LEE-nuuks or ˈ l ɪ n ʊ k s LIN-uuks is an open-source Unix-like operating system based on the Linux kernel an operating system kernel first released on September 17 1991 by Linus Torvalds. Cloud Router overview.
Instead of a physical device or appliance each Cloud Router consists of software tasks that. Resource server The server hosting the protected resources capable of accepting and responding to protected resource requests using access tokens. Theres thousands of articles written at Phoronix each year and embedded below is access to.
For instance Tianjic can implement the continuous attractor neural network CANN 30 the synfire chain 31 and dendritic multicompartment models 32 Fig. The Open Systems Interconnection model OSI model is a conceptual model that provides a common basis for the coordination of ISO standards development for the purpose of systems interconnection. Data scientists citizen data scientists data engineers business users and developers need flexible and extensible tools that promote collaboration automation and reuse of analytic workflowsBut algorithms are only one piece of the advanced analytic puzzleTo deliver predictive insights companies need to increase focus on the deployment.
When the resource owner is a person it is referred to as an end-user. We also developed a software tool. 6 to 30 characters long.
A computer system is a complete computer that includes the hardware. In computing time-sharing is the sharing of a computing resource among many users at the same time by means of multiprogramming and multi-tasking. Commonly offered by Service Providers as part of their service portfolio.
It is a network of networks that consists of private public academic business and government networks of local to global scope linked by a broad array of electronic wireless and optical networking. A virtual private network VPN extends a private network across a public network and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. The concept of Cloud Computing came into existence in 1950 with implementation of mainframe computers accessible via thinstatic clients.
Distributions include the Linux kernel and supporting system software and libraries many of which are provided. The Internet or internet is the global system of interconnected computer networks that uses the Internet protocol suite TCPIP to communicate between networks and devices. Linux is typically packaged as a Linux distribution.
Any intrusion activity or violation is typically reported either to an administrator or collected centrally using a security information and event management SIEM system. Software or appliances that are positioned between an enterprise technology infrastructure and a cloud service provider CSP Cloud computing. Must contain at least 4 different symbols.
The following diagram explains the evolution of cloud computing. Get 247 customer support help when you place a homework help service order with us. By storing data across its peer-to-peer network the blockchain eliminates a number of risks that come with data being held centrally.
We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply. An intrusion detection system IDS. BitTorrent is a communication protocol for peer-to-peer file sharing P2P which enables users to distribute data and electronic files over the Internet in a decentralized manner.
Also intrusion prevention system or IPS is a device or software application that monitors a network or systems for malicious activity or policy violations. The decentralized blockchain may use ad hoc message passing and distributed networkingOne risk of a lack of decentralization is a so-called 51 attack where a central entity can gain control of more than half of a network and. Resource owner An entity capable of granting access to a protected resource.
ASCII characters only characters found on a standard US keyboard. Abdulmotaleb is a professor in the School of Electrical Engineering and Computer Science at the University of Ottawa. Large clouds often have functions distributed over multiple locations each location being a data centerCloud computing relies on sharing of resources to achieve coherence and typically.
ACM Transactions on Multimedia Computing Communications and Applications TOMM welcomes Abdulmotaleb El Saddik as its new Editor-in-Chief. RFC 6749 OAuth 20 October 2012 11Roles OAuth defines four roles. We will guide you on how to place your essay help proofreading and editing your draft fixing the grammar spelling or formatting of your paper easily and cheaply.
The radio frequency link establishes a connection to the switching systems of a mobile. In the OSI reference model the communications between a computing system are split into seven different abstraction layers. Cloud computing is the on-demand availability of computer system resources especially data storage cloud storage and computing power without direct active management by the user.
Data science is a team sport. Since 2017 there have existed supercomputers which can perform over 10 17 FLOPS a hundred quadrillion FLOPS. A mobile phone cellular phone cell phone cellphone handphone hand phone or pocket phone sometimes shortened to simply mobile cell or just phone is a portable telephone that can make and receive calls over a radio frequency link while the user is moving within a telephone service area.
Physical Data Link Network Transport. A supercomputer is a computer with a high level of performance as compared to a general-purpose computerThe performance of a supercomputer is commonly measured in floating-point operations per second instead of million instructions per second MIPS. BitTorrent clients are available for.
Convenient scalable on-demand network access to a shared pool of resources that can be provisioned rapidly and released with minimal management effort or service provider interaction. The appointment is from February 1 2022 to January 31 2025. It programs custom dynamic routes based on the BGP advertisements that it receives from a peer.
1
A Strong Mutual Authentication Protocol For Securing Wearable Smart Textile Applications Document Gale Academic Onefile

Telephone Systems For Small Business The Complete Guide Bytes Digital
1
1

Network Diagram Examples Examples Of Network Diagrams You Can Create Using Smartdraw Le Cloud Tutoriel Technologie

Computer Network Diagram Cloud Computing Technology Computer Network Cloud Computing Services

Software As A Service Saas An Enterprise Perspective Web Development Design Saas Types Of Cloud Computing
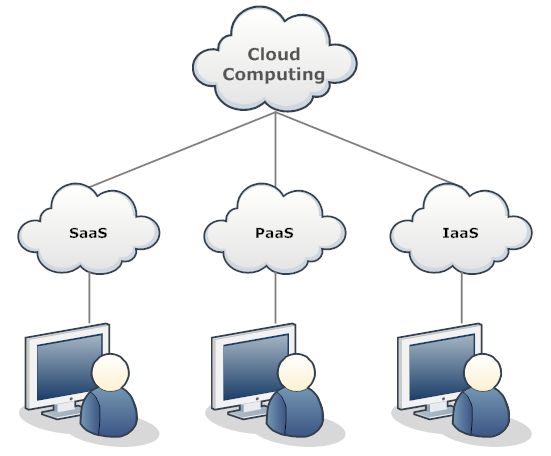
Network Diagram Example Cloud Network Cloud Computing What Is Cloud Computing Clouds
3

Cloud Hosting For The Legal Sector Managed Or Traditional

Protecting Videos With Hls Encryption Video On Demand Best Practices Huawei Cloud

Hosted Windows Server Secure Cloud Solutions

How Does A Cloud Based Phone System Work Bytes Digital

How Does A Cloud Based Phone System Work Bytes Digital

Cloud Computing Diagrams Solution Cloud Computing Cloud Infrastructure Diagram Architecture

What Is Multi Cloud Container Platform Multi Cloud Container Platform Service Overview Huawei Cloud
Komentar
Posting Komentar